Almost Leaked My Key—Thank God for GitGuardian
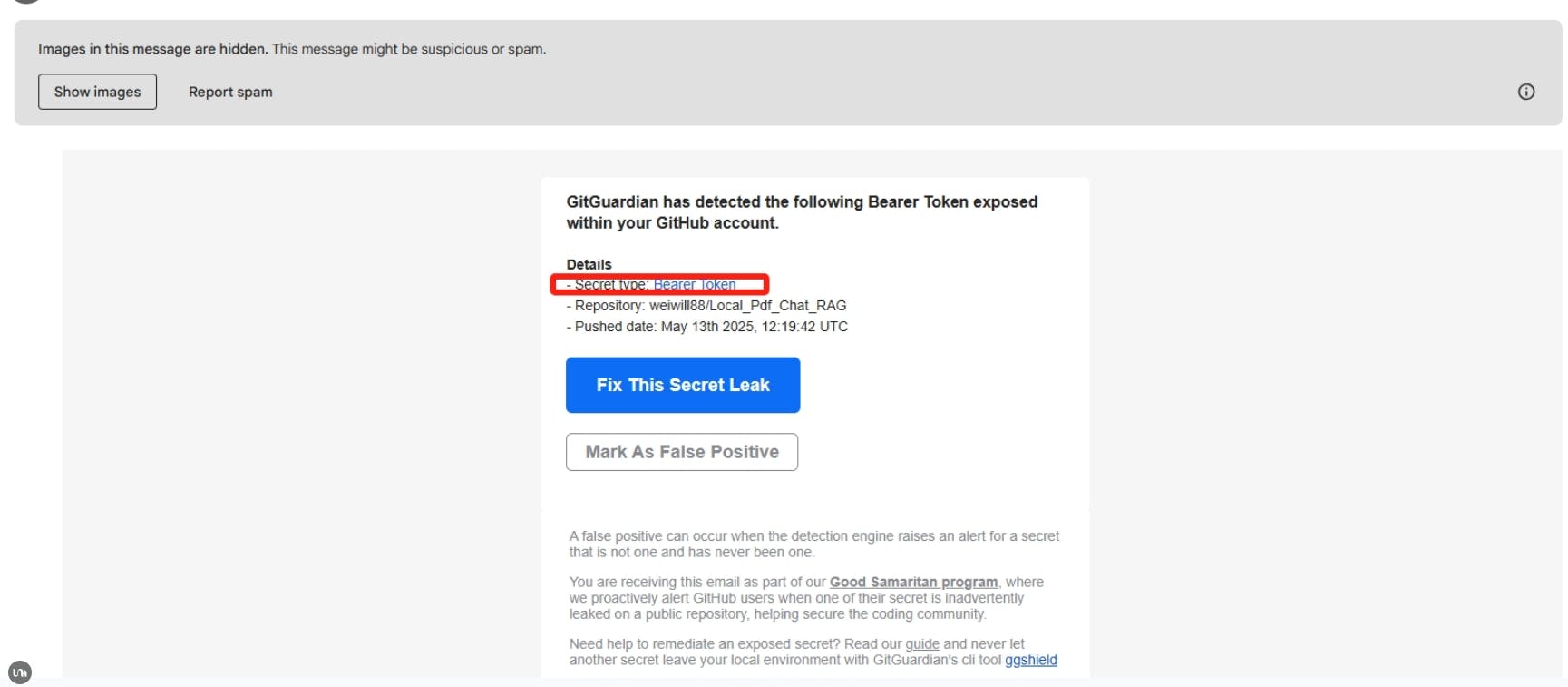
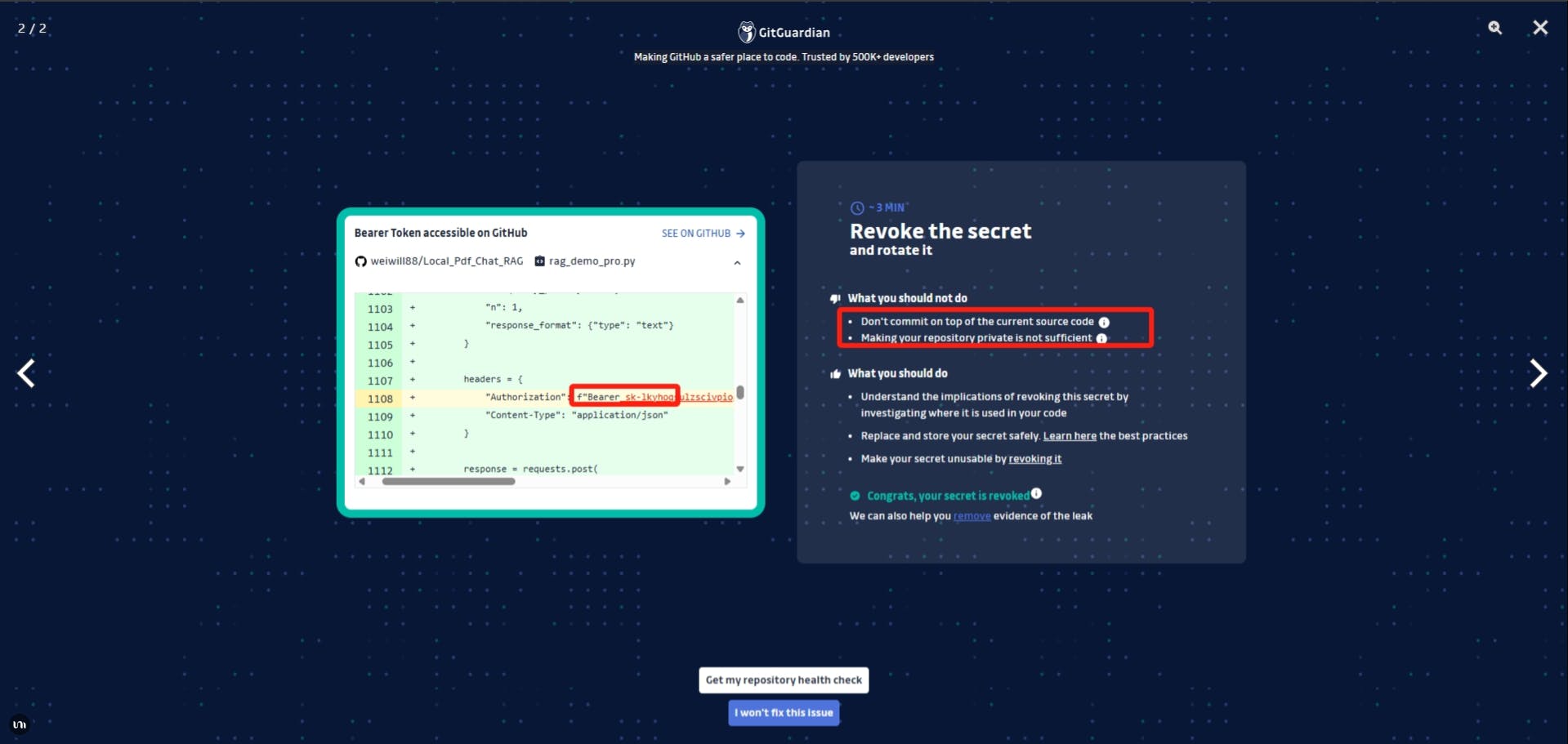
This morning I opened my inbox to find an alert from GitGuardian about a leaked key. My first thought: “Great, another phishing email.” Nearly deleted it on the spot. Then I realized—yesterday when I was using Cursor to bulk-update my scripts, I’d left the API key in plain text…
Why did I do this?
I’m using Cursor to speed up script edits and testing endpoints—having the key in the code felt “convenient.”
But convenience often comes at the cost of security, and this time I sacrificed security for speed.
Where I’m at now:
Revoked that exposed key and generated a new one—urgently.
Shifted all secrets into environment variables, removing them from code.
Planning to integrate the GitGuardian CLI into my CI/CD pipeline to catch leaks before they ever reach my inbox.
Real talk: Getting this alert was both embarrassing and a huge relief—lesson learned!Next steps I’m curious about:
What lightweight secret-management tools do you trust?
How do you avoid the “oops, I forgot to remove the credentials” trap in your workflow?
Drop your tips, war stories, or suggestions in the comments—let’s co-create a safer, more efficient dev process together!


Replies
StreamAlive
Happens to the best of us! 🤣🤣
Oof, been there, had a close call with a hardcoded key myself. Now I always use env variables and run a quick scan before pushing. Definitely curious what lightweight tools others are using too!